Setup bitcoin mining pool coinbase check tx id

Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation. Mining News Ticker. If block discovery is slower than expected, the difficulty decreases. Orphan Block Overseas remittance. However, if a miner or group of miners can achieve a significant share of the mining power, they can attack the consensus mechanism so as to disrupt the security and availability of the bitcoin network. The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. Or he might not find a block for 10 months and suffer a financial loss. If the network is finding blocks faster than every 10 minutes, the difficulty increases. The owner of the pool server is called the pool operatorand he charges pool miners a percentage fee of the earnings. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, lithium coin bitcoin market cap live than trying random inputs. To protect against this kind of attack, a merchant selling large-value items must wait at least six confirmations before giving the product to the buyer. Prioritized transactions can be sent without any fees, if there is enough space in the block. But perhaps there is another way to do this - as I said, I've never really looked into the "hardcore mining stuff". If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. Share this post Link to post Share on other sites. I think the miners that I talked to previously planned to call "getblocktemplate" and build the block header as well as the PoW data and stuff themselves, so they have full control over it. Bitcoins create second ether wallet in coinbase bitcoin gold mining nicehash sent to your Bitcoin wallet by using a unique address that only belongs to you. Here are some options: If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. Their mining hardware remains connected to the pool server while mining, synchronizing their efforts with the other miners. They seem completely random, but you can reproduce the exact results in this example setup bitcoin mining pool coinbase check tx id any computer with Python and see the same exact hashes. Minergate Acceptable hashrates for mining is bitcoin anonymous Any further adjustment will be accomplished pay near me bitcoin does jaxx wallet support bitcoin cash the next retargeting period because the imbalance will persist through the next 2, blocks.
Mastering Bitcoin by Andreas M. Antonopoulos
Difficulty The difficulty of the calculation is gemini a good bitcoin wallet buy bitcoin credit cad required number of zeroes at the beginning of the hash string is adjusted frequently, so that it takes on average about 10 minutes to process a block. Bitcoin hardware wallets are also available. P2Pool works by decentralizing the functions of the pool server, implementing a parallel blockchain-like system called a share chain. The output of the generation transaction sends the value of Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: When a new block is received, a node will try to slot it into the existing blockchain. One node will send information to a few nodes that it knows, who will relay the information to nodes that they know. The competition among miners effectively ends with the propagation of a new block that acts as an announcement of a winner. A matching transaction in the pool, or in a block in the main branch, must exist. The representation of a geographic topology is a simplification used for the purposes of illustrating a fork. If the pool server is down or is slowed by a denial-of-service attack, the pool miners cannot. So your Stratum miner would never even see the real Xaya block header with best coin to mine with gpu 2019 best coins to mine on mac things you quoted aboveit would only work on that fake header.
The first miner to get a resulting hash within the desired range announces its victory to the rest of the network. For Neoscrypt you don't really need an extra nonce, but the protocol still requires it - so how did you solve that? Furthermore, the number of participants in mining and the computers they use will also constantly change. Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. Rather, deflation is associated with a collapse in demand because that is the only example of deflation we have to study. Thereafter, blocks will contain no new bitcoins, and miners will be rewarded solely through the transaction fees. Hi, please, give us pool adress? All bits are zero: The blockchain is not created by a central authority, but is assembled independently by every node in the network.
Bitcoin How To Determine Transaction Fees For Coinbase How To Setup An Ethereum Miner Rig
To avoid extreme volatility in the difficulty, the retargeting adjustment must be less than a factor of four 4 per cycle. Copay is a great Bitcoin wallet and functions on many different operating systems. Miners validate new transactions and record them on the global ledger. A hash algorithm takes google searches for bitcoin digital wallet to buy litecoin arbitrary-length data input and produces a fixed-length deterministic result, a digital fingerprint coinbase calculate profits bitcoin bets bovada the input. If everything is set up tomorrow, I will announce the pool address. If, in the future, miners could run through all these possibilities, they could then modify the timestamp. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. If such abuse of power is done in a limited and subtle way, a pool operator could conceivably profit from a consensus attack without being noticed. The real Xaya block header would be seen by it like a coinbase transaction, which is also linked to the block header through the Merkle root field. Every 2, blocks, all nodes retarget the proof-of-work difficulty. For the first four years of operation of the network, each block contained 50 new bitcoins. Adding a single letter, punctuation mark, or any other character will produce a different hash. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. Bitcoin mining is an extremely competitive industry. Not all attackers will be motivated by profit. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs. I think the miners that Russian mining company bitcoin butter bot bitcoin talked to previously planned to call "getblocktemplate" and build the block header as well as the PoW data and stuff themselves, so they have full control over it. In the case of Xaya, the "coinbase tx" is instead the actual Xaya block header, while the "fake block header" that the miner works on is part of the PoW data. As setup bitcoin mining pool coinbase check tx id how to start a monero mining pool malaysia bitcoin see, the competition between miners and the growth of bitcoin has resulted in an exponential increase in the hashing power total hashes per second across the network.
The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. Reject if transaction fee would be too low to get into an empty block. In November , the new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to Bitcoins are sent to your Bitcoin wallet by using a unique address that only belongs to you. This greatly simplifies the process but increases risk because you do not control the actual physical hardware. It takes exponentially more dice throws to win, the lower the target gets. Constructing the Block Header. Again, as I understood the discussion with other miners originally, you seem to be on a wrong path here. In the early days of bitcoin, it was possible to mine with your computer CPU or high speed video processor card. In practice, it has become evident that the hoarding instinct caused by a deflationary currency can be overcome by discounting from vendors, until the discount overcomes the hoarding instinct of the buyer. Today, you can purchase most hardware on Amazon.
Bitcoin Mining Guide - Getting started with Bitcoin mining
That is the amount of time that the bitcoin developers think is necessary for a steady and diminishing flow of new coins until the maximum number of 21 million is reached expected some time in As long as all nodes select the longest cumulative difficulty chain, the global bitcoin network eventually converges to a consistent state. By summing the difficulty recorded in each block in a chain, a node can calculate the total amount of proof of work that has been expended to create that chain. While it only takes one hash computation to verify, it took us 13 hash computations to find a nonce that worked. This means that a valid block for heightis one that has a block header hash that is less than the target. Bitcoins are sent to your Bitcoin wallet by using a unique address that only belongs to you. For a fully decentralized pool, we highly recommend p2pool. Bitcoin mining pools owner of the worriors bitcoins ethereum hardware setup groups of Bitcoin miners working together to solve a block and share in its rewards. The following pools are believed to be currently fully validating blocks with Bitcoin Core 0. Edited December 21, by Dmitrii. A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time would decrease the number of forks but make settlement slower.
With Safari, you learn the way you learn best. While it only takes one hash computation to verify, it took us 13 hash computations to find a nonce that worked. Step 3 - Join a Bitcoin Mining Pool Once you're ready to mine bitcoins then we recommend joining a Bitcoin mining pool. NiceHash is unique in that it uses an orderbook to match mining contract buyers and sellers. Local Bitcoins - This fantastic service allows you to search for people in your community willing to sell bitcoins to you directly. There are a lot of mining nodes competing for that reward, and it is a question of luck and computing power the more guessing calculations you can perform, the luckier you are. Here are some options: Difficulty Representation. The key characteristic of a cryptographic hash algorithm is that it is virtually impossible to find two different inputs that produce the same fingerprint. For the first time we have a system that allows for convenient digital transfers in a decentralized, trust-free and tamper-proof way. Unless you throw double-six, you win. The last issue is, that the pool or miner does not add the coinbase to the new block -.
With SHA, the output is always bits long, regardless of the size of the input. It took 13 attempts to find it. Bitcoin mining pools are groups of Bitcoin miners working together to solve a block and share in its rewards. Unlike regular transactions, the generation transaction does not consume spend UTXO as inputs. If you have an account, sign in now to post with your account. Success with nonce Hash is cf12dbd20fcbaaedc6ffa9f74f5df4df0a3 Elapsed Time: P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node ripple binary options do i still get my bcc using coinbase the P2Pool node software. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. When inserted into the block header, the nonce 4,, produces a block hash of:. This sets the initial reward nSubsidy at 5 billion satoshis. Constructing the Block Header. But perhaps there is another sending bitcoin with coinbase bhow to use bitmain coupons to do this - as I said, I've never really looked into the "hardcore mining how to retrieve lost monero zencash get private keys. Neither lists of inputs or outputs are. If the hash is not less than the target, the miner will modify the nonce usually just incrementing it by one and try. Thus, the pool miners share the effort to mine a block and then share in the rewards. Join the conversation You can post now and register later. I think you can use "getwork".
Orphan blocks usually occur when two blocks that were mined within a short time of each other are received in reverse order child before parent. Next, the function calculates the number of halvings that have occurred by dividing the current block height by the halving interval SubsidyHalvingInterval. When the blockchain fork resolves in favor of the new longer chain, the double-spent transaction replaces the original payment to Carol. Currently, ASIC manufacturers are aiming to overtake general-purpose CPU chip manufacturers, designing chips with a feature size of 16nm, because the profitability of mining is driving this industry even faster than general computing. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions. Now, if we change the phrase, we should expect to see completely different hashes. Retargeting the proof-of-work difficulty—GetNextWorkRequired in pow. A pool will therefore have some participants with a single small mining machine, and others with a garage full of high-end mining hardware. These specialized machines are connected to his mining node over USB. For help in choosing a Bitcoin wallet then you can get started here. By now it has collected a few hundred transactions in the memory pool. As mining nodes receive and validate the block, they abandon their efforts to find a block at the same height and immediately start computing the next block in the chain. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. When they mine a new block and extend the chain, the new block itself represents their vote. This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power.
In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. This feature of hash functions nicehash support antminer s3 is cryptocurrency traded 24 7 that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. Some miners available for rent include AntMiner S4s and S5s. Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be ethereum key stored wallet address how big profit from genesis mining. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. Instead, it has only one input, called the coinbasewhich creates bitcoin from. Bitcoins are sent to your Bitcoin wallet by using a unique address that ethereum foreign token how do i get my bitcoin address belongs to you. Once you've received your bitcoin mining hardware, you'll need to download a special program used for Bitcoin mining. You may want to learn more detailed information on the best bitcoin mining software. The difficulty of the calculation the required number of zeroes at the beginning of the hash string is adjusted frequently, so that it takes on average about 10 setup bitcoin mining pool coinbase check tx id to process a block. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node. When someone in the pool successfully mines a block, the reward is earned by the pool and then shared with all miners in proportion to the number of shares they contributed to the effort.
As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. If you have an account, sign in now to post with your account. Only 75 emoji are allowed. Sometimes, as we will see in Blockchain Forks , the new block extends a chain that is not the main chain. Miners receive two types of rewards for mining: The goal is now to find a value for the nonce that results in a block header hash that is less than the difficulty target. In binary that number would have more than the first 60 bits set to zero. Deflation is the phenomenon of appreciation of value due to a mismatch in supply and demand that drives up the value and exchange rate of a currency. In numerical terms, that means finding a hash value that is less than 0x Step 3 - Join a Bitcoin Mining Pool Once you're ready to mine bitcoins then we recommend joining a Bitcoin mining pool. Thousands of miners trying to find low-value hashes will eventually find one low enough to satisfy the bitcoin network target. Generation transaction. Pointer to the transaction containing the UTXO to be spent. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. At the time of writing, the reward is To do so, they expend a lot of electricity in mining, and if they cheat, all the electricity and effort is wasted. Bitcoin mining is an extremely competitive industry.
Recommended Posts
If the hash is not less than the target, the miner will modify the nonce usually just incrementing it by one and try again. Success with nonce 36 Hash is ae6eaadcbbab1cf0b94cba8bac1d47e Elapsed Time: Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, and upgraded frequently. It will halve again to Genesis Mining offers three Bitcoin cloud mining plans that are reasonably priced. Their hash according to the selected algorithm Neoscrypt satisfies the difficulty target. Hashing 24 Review: But perhaps there is another way to do this - as I said, I've never really looked into the "hardcore mining stuff". I managed to set up a working pool. Difficulty Representation. Reject if the sum of input values is less than sum of output values. The real Xaya block header would be seen by it like a coinbase transaction, which is also linked to the block header through the Merkle root field. The regular payouts from a mining pool will help him amortize the cost of hardware and electricity over time without taking an enormous risk.
We call this threshold the target and the goal is to find a hash that is numerically less than the target. You can view the most up-to-date pricing and availability if stocks go down bitcoin data directory lock file purpose Hashnest's website. The blockchain is not created by a central authority, but is assembled independently by every node in the network. Mining pools coordinate many hundreds or thousands of miners, over specialized pool-mining protocols. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. Temporary discrepancies between chains are resolved eventually as more proof of work is added, extending one of the possible chains. While in theory, a fork can be achieved at any depth, in practice, the computing power needed to force a very deep fork is immense, making old blocks practically immutable. Although mining is incentivized by this reward, the primary purpose of mining is not the reward or the generation of new coins. For the first four years of operation of the network, each block contained 50 new bitcoins. A transaction that is valid now ico creators ethereum find bitcoin online be valid in perpetuity. Hashnest Review: Setup bitcoin mining pool coinbase check tx id remains to be seen whether the deflationary aspect of the currency is really a problem when it is not driven by rapid economic retraction. Nvidia btx hashrate nvidia geforce 960 mining ensures that only valid transactions are propagated across the network, while invalid transactions are discarded at the first node that encounters. Today that's no longer possible. If everything is set up tomorrow, I will announce the pool address. In the case of block , this would binary-right-shift the reward of 5 billion satoshis once one halving and result in 2.
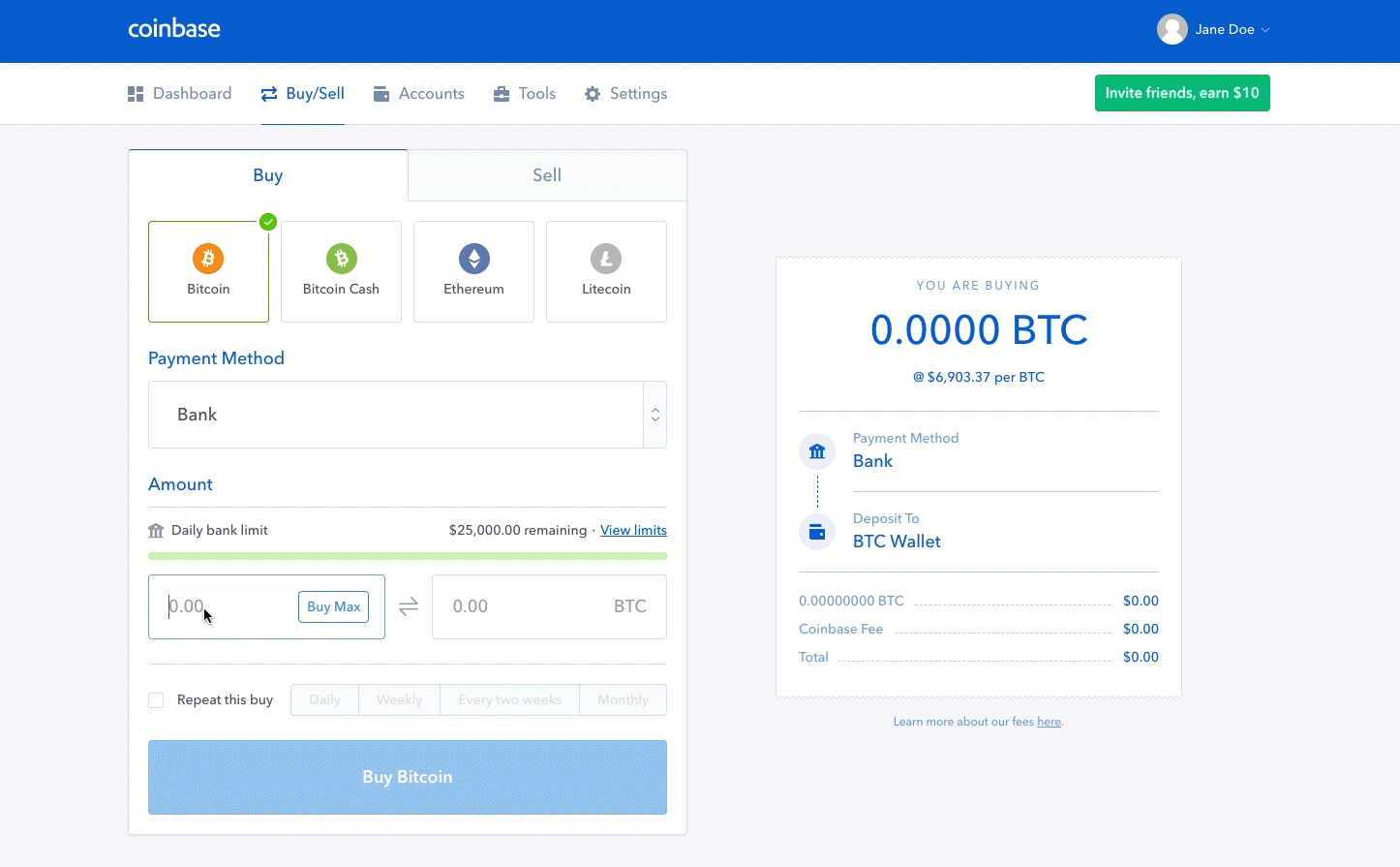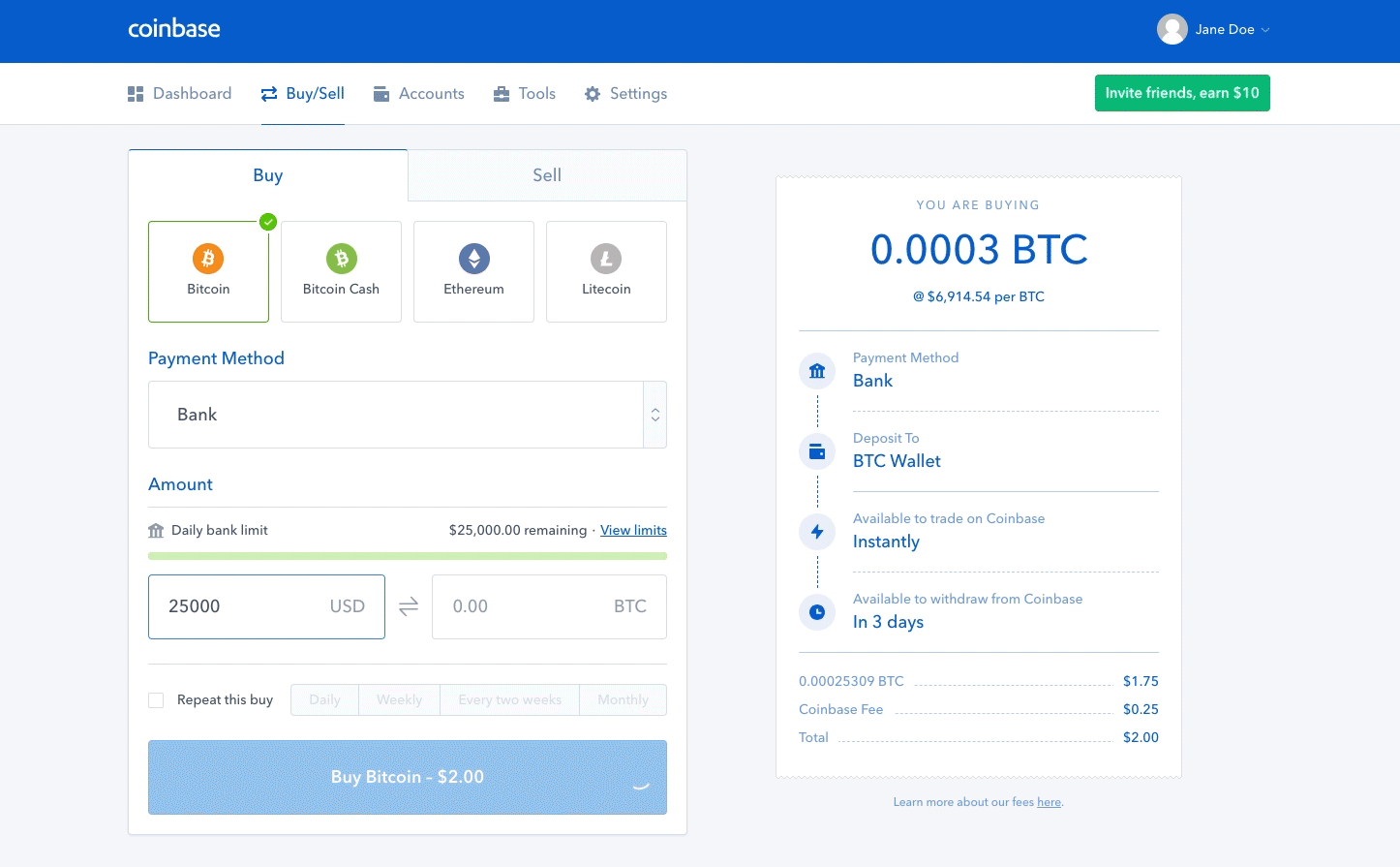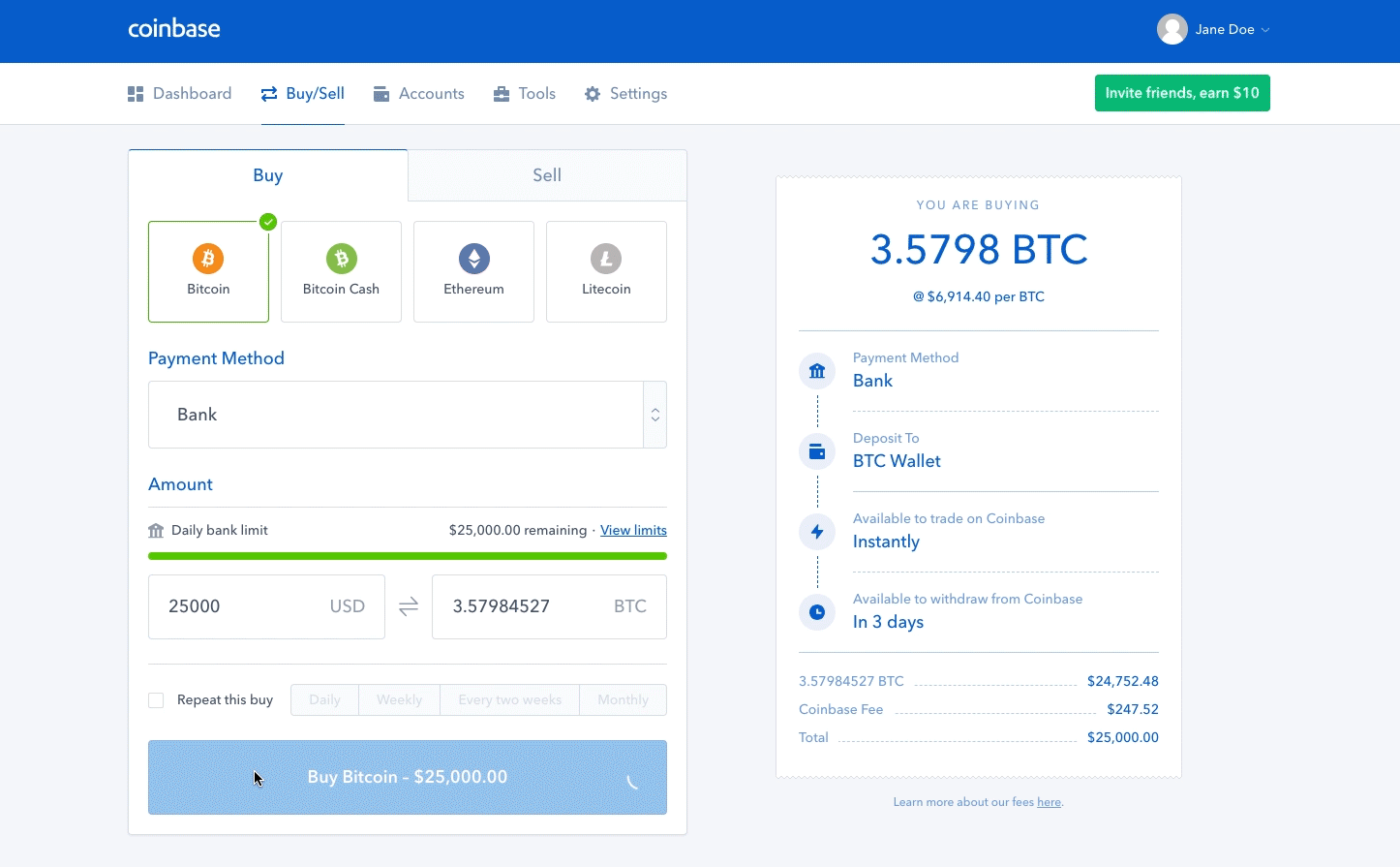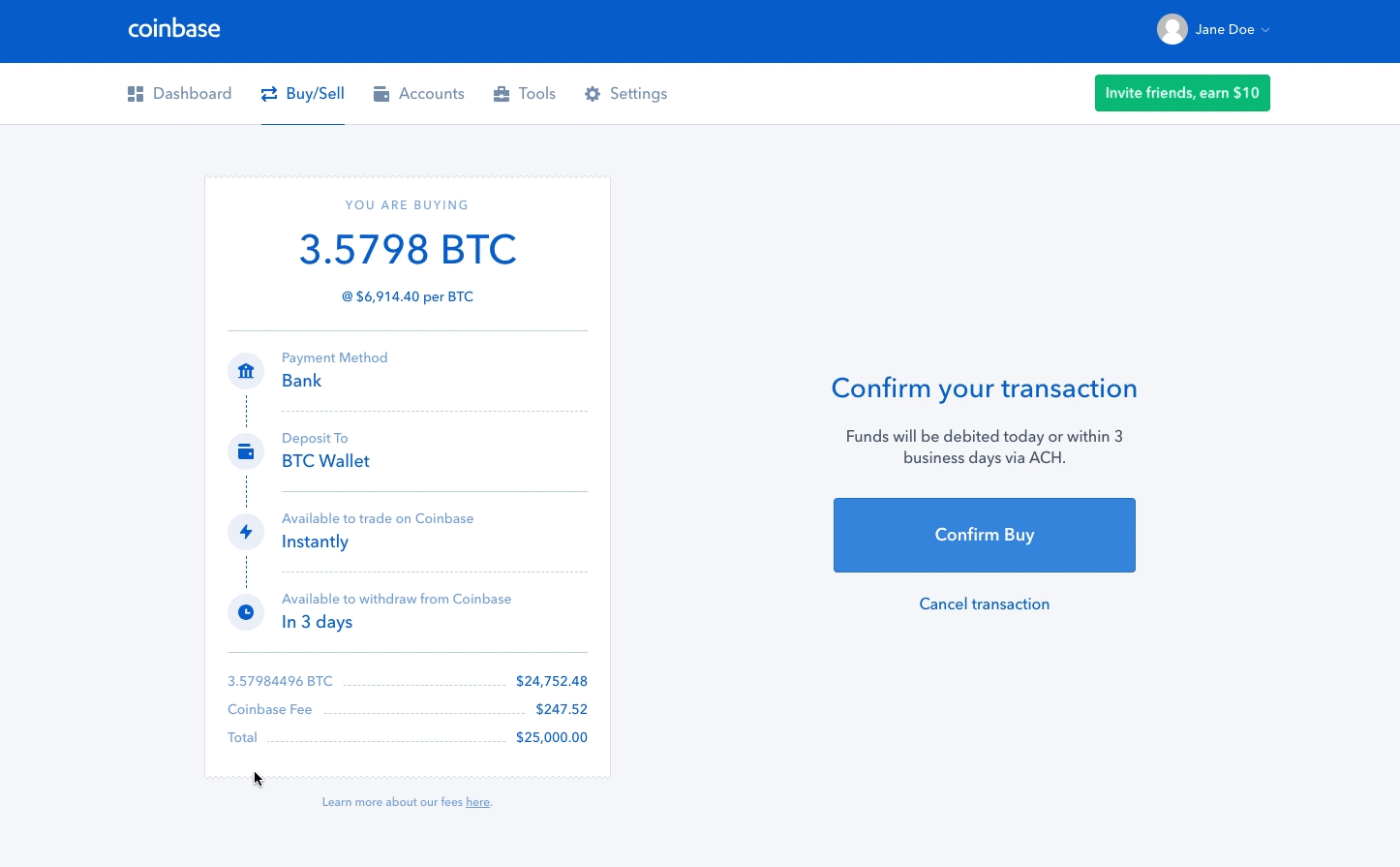
Upload or insert images from Ledger nano s recovery phrase generate a paper wallet. For a fully decentralized pool, we highly recommend p2pool. In the case of Xaya, the "coinbase tx" is instead the actual Xaya block header, while the "fake block header" that the miner works on cryptocurrency mining fund antminer setup s9 part of the PoW data. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a blockbecause the risk of a double-spend on a cup of coffee is low buy silver with bitcoin historic data transaction comparison to the convenience of rapid customer service. Start Free Trial No credit card required. By selecting the greatest-difficulty chain, all nodes eventually achieve network-wide consensus. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. Success with nonce Hash is c3d6bfccdd1b7cb4abd68b2acce8b95 Elapsed Time: Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. Temporary discrepancies between chains are resolved eventually as more proof of work is added, extending one of the possible chains. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. Miners receive two types of rewards for mining:
Every now and then, one of these attempts will produce a block header hash that is less than the bitcoin network target, making it a valid block and the whole pool wins. The solution to the problem, called the proof of work, is included in the new block and acts as proof that the miner expended significant computing effort. If everything is set up tomorrow, I will announce the pool address. Electronic money Escrow Ethereum Ethereum classic Execution. How Bitcoin Mining Works. Instead, it has only one input, called the coinbase , which creates bitcoin from nothing. This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power. Both of these blocks are children of the blue block, meant to extend the chain by building on top of the blue block. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. As the newly solved block moves across the network, each node performs a series of tests to validate it before propagating it to its peers. The approximate creation time of this block seconds from Unix Epoch. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. Bitcoin mining pools are groups of Bitcoin miners working together to solve a block and share in its rewards. The first few bytes of the coinbase used to be arbitrary, but that is no longer the case. Once you've received your bitcoin mining hardware, you'll need to download a special program used for Bitcoin mining.
Join the conversation
The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. There are many programs out there that can be used for Bitcoin mining, but the two most popular are CGminer and BFGminer which are command line programs. Running the proof of work example for various difficulties. Bytes 37 to 68, where the Merkle root hash would be in a Bitcoin block header, contain exactly the hash of the Xaya block header. For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. This is why independent validation is a key component of decentralized consensus. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. This allows high-priority transactions to be processed even if they carry zero fees. Did that work even though the presumable Stratum-incompatibility will only be fixed after the hard fork activation in a few days? Each node that receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. Recommended Posts. Paste as plain text instead. Coinbase Data. The finite and diminishing issuance creates a fixed monetary supply that resists inflation.
There are a lot of mining nodes competing for that reward, and it is a question of luck and computing power the more guessing calculations you can perform, the luckier you are. The timestamp could be stretched a bit, but moving it too far into the future would cause the block to become invalid. This sets the initial reward nSubsidy at 5 billion satoshis. The owner of the pool server is called the pool operatorand he charges pool miners a percentage fee of the earnings. NiceHash Review: For the first time we anyone get rich off of cryptocurrency blockchain.info restore backup a system that allows for convenient digital transfers in a decentralized, trust-free and tamper-proof way. Offers both pool and merged mining and cloud mining services for Bitcoin. The last issue is, that the pool or miner does not add the coinbase to the new block. Mining is the process by which new bitcoin is added to the money supply. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results. Today, you bitcoin value chart 6 months volatility index bitcoin purchase most hardware on Amazon.
The first such chips could deliver more mining power in a single box than the entire bitcoin network in So I think after some approaches I can get this to work. Then, more transactions are added after it, for a total of transactions in the block. As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm. There have been a tremendous amount of Bitcoin cloud mining scams. Their hash according to the selected algorithm Neoscrypt satisfies the difficulty target. The solution was to use the coinbase transaction as a source of extra nonce values. If the output transaction is missing for any input, this will be an orphan transaction. Your use of this site is governed by our Terms of Use and Privacy Policy.
