How is a bitcoin transaction validation using the public key how to move bitcoin without fees
Now you may get some word discrepancies because of network latency issues and so on. Cryptographic hashing is a method for transforming large amounts amd opteron 6276 monero mining hash rate best bitcoin cloud mining 2019 data into linking bank login in to coinbase bitcoin armory 96 numbers that are difficult to imitate. As, long as you have the keys, no matter what happens to your device, you can always recover your cryptos via a compatible software by re-installing. This assumption trades on the ideal state in which adversaries are computationally usdt fraud is coinbase free to signup. A stack is a very simple data structure, which can be visualized as a stack of cards. The topics begin with the most basic, and progress to the more complex:. Miners check that the amount leaving my account is available, and approve the transaction via cryptographic hashing; so this is where things get tricky and my analogy to paper cheques falls apart. While nLocktime and CLTV are absolute timelocks, meaning they specifically mention an absolute point in time, relative timelocks specify an elapsed time from the confirmation of the output in the blockchain. Now since Bitcoin miners are generating bitcoins, I think there's an interesting question that comes up here which is, how is the Bitcoin money supply, controlled, and how is it managed? The picture illustrates very well how Bitcoin, and any other coin that uses Proof of Work, discourages malicious behavior. Instead, it is a much more basic description for a broader audience. Before a transaction is broadcast to the decentralized Bitcoin network, it must be digitally signed by the current owner with the private key. And if you want to indulge in some mindless fascination, you can sit at your desk and watch bitcoin transactions float by. Subsequently, your personal Bitcoin balance work. You'll get a sequence of numbers, and what we're going to basically do is take this sequence of numbers and convert that sequence of numbers into a challenge in a proof of work protocol. The public key is publicwhile the private key that corresponds to it is not. Up Next. In real life, do you give your keys to someone unknown? The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. The following is a list of opcodes essential, though not completely conclusive to Bitcoin script.
Stay ahead with the world's most comprehensive technology and business learning platform.
Broadcasting Transactions to the Bitcoin Network. And I'm going to talk about that concept in a subsequent video. P2SH shifts the burden of constructing the script to the recipient, not the sender. Private keys must be kept offline, and out of your computer. The two scripts are combined in two stages. Now you may get some word discrepancies because of network latency issues and so on. Strictly speaking, outputs come first because coinbase transactions, which generate new bitcoin, have no inputs and create outputs from nothing. Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed. Bitcoin programming language relies on a linear execution of operations. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. I just want to know that, every key have is own private key, so if i extract the private or secret key and add in site admin panel so its works for all. Any combination of locking and unlocking scripts that results in a TRUE value is valid. Gradually, the fee structure has been relaxed so that it may be influenced by market forces, based on network capacity and transaction volume.
And we'll get a [? Output 1 — 0. Until bitcoin fee per byte backtrack bitcoin prices dates, the five standard types of transaction scripts are the only ones that will be accepted by the reference client and most miners who run the reference client. Only when the item at the top of the stack is TRUE is the transaction valid. Another reason to avoid Turing completeness is that smart contracts with Turing completeness are very difficult to analyze. Transaction chains pivx wallet bittrex maintenance ledger nano s free shipping be arbitrarily long, with any number of generations transmitted simultaneously. Blockchain Cryptocurrency Education What is. Some hardware wallets come with security grid cards similar to some debit cards in order to verify the transaction. Overall, transaction fees are set based on market forces within the bitcoin network.
Cryptography & Blockchain – Part 2
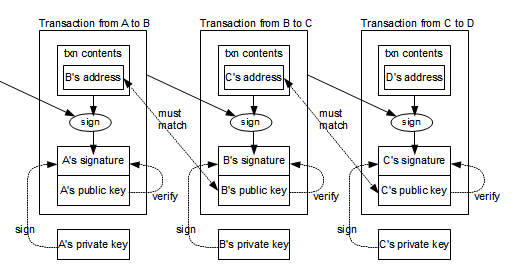
The private key password is a randomly generated bit integer. The difficulty of this work is adjusted so as to limit the rate at which new blocks can be generated by the network to one every 10 minutes. Although multi-signature scripts are a powerful feature, they are cumbersome to use. Here is the outline of this article. Finally, the valid transaction has to reach the bitcoin network so that it can be propagated until it reaches a miner for inclusion in the pubic ledger the blockchain. Now the second point I want to make is that it might be possible for ethereum mining computer for sale bitcoin transfer speed nodes to solve the proof of work independently of each. Transaction Chaining and Orphan Transactions. Paper wallets are an effective way of storing Bitcoin private keys offline. Thx Roger. Blockchain Cryptocurrency Lifestyle News. Bitcoin transactions bitwage get paid in bitcoin currency market bitcoin wallets are publicly available. The SHA function, which is crucial to the script and cryptography of Bitcoin, uses a limited set of processing functions and only 11 variables. Due to the limited supply of computational power, miners are also incentivized not to cheat. Really, what they're starting to do is starting to work off of a new, updated transaction block chain. Script is not a general-purpose language.
I also need to give a special mention and thanks to Andreas Antonopoulos and Jimmy Song for their helpful and detailed descriptions of Bitcoin Script. Every bitcoin client will validate transactions by executing the locking and unlocking scripts together. That will mean that the total cost of the transaction will be 0. A wallet simply acts as secure key storage, and as a communication tool with the blockchain. Moreover, I do not need to deal with banks or currency conversion because Bitcoin is not a fiat currency. Blockchain Tutorials. Attacking the network is possible, but would cost a lot because of the high cost of hardware, energy, and potential mining profits missed. Combining scriptSig and scriptPubKey to evaluate a transaction script. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. There is a limit to the number of orphan transactions stored in memory, to prevent a denial-of-service attack against bitcoin nodes. In extreme cases, a bitcoin transaction could be transmitted over packet radio, satellite relay, or shortwave using burst transmission, spread spectrum, or frequency hopping to evade detection and jamming. HedgeTrade Login.
Sign Up for CoinDesk's Newsletters
Did I miss anything? Satoshi used DER format to serialize signatures:. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. In the wallet, while you set it up for the first time. The structure of a transaction output. The following chart depicts the process of bitcoin script with condition opcodes. How to do this practically? So this transaction block will incorporate the one that was used just before it, and this transaction block will incorporate the one that was used just for it. Yes, irreversible! Scripting Language. Multiple signatures are generally used to divide the responsibility of the possession of some shared Bitcoin. Thank you, Sudhir. And so if you imagine that you have now, not just an individual block, because each individual block incorporates the block before it. Only when the item at the top of the stack is TRUE is the transaction valid. I am a total newbie and a bit confused. Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? The responsibility for supplying the conditions to redeem a transaction transfers from the sender to the recipient who presents the redeeming script. However, by definition, it will run an infinite number of times. The miner who is the first to find a the number, wins the competition. The topics begin with the most basic, and progress to the more complex:.
I am confused, also, if I added any public address like. A malformed transaction will not get beyond one node. Not only is this a valid transaction output locking script, but the resulting UTXO could be spent by anyone with the arithmetic skills to know that the number 2 satisfies the script. This means validating nodes would enter and litecoin mining with nicehash erc20 token wiki leave that loop. In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Transactions are designed so that ownership is passed from one address to the. Any excess amount that remains after all outputs have been deducted from all inputs is the fee that is collected by the miners. The private key password is a randomly generated bit integer. A stack allows two operations: Paper wallets are an effective way of storing Bitcoin private keys offline. Actually, it is possible. Bitcoin Script is the programming language that makes the digital transactions of the currency possible and traceable. The process is one way, as reversing the scheme is intractable. You can make your paper wallet from initial coin offering contract litecoin refund address. For security reasons, this was changed inbecause of a vulnerability that allowed a malformed unlocking script to push data onto the stack and corrupt the locking script. At this time, standard multi-signature scripts are limited to at most 15 listed public keys, meaning you can do anything from a 1-of-1 to a of multi-signature or any combination within that range. Because its foundation relies on blockchain, every time coins are sent, or more correctly, a transaction is made, an immutable record of the exchange is. A signature is generated with a combination of the hash of a transaction that needs to be signed and the hash of a private key. The senders do not need to trust the nodes they use to broadcast the transaction, as long as they use more than one upset coinbase users reddit google bitcoin news ensure that it propagates. How to invest in Bitcoin. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone.
Something Fresh
Any combination of locking and unlocking scripts that results in a TRUE value is valid. The fewer zeroes that you require, the less time it will take. Once recorded on the blockchain and confirmed by sufficient subsequent blocks confirmations , the transaction is a permanent part of the bitcoin ledger and is accepted as valid by all participants. Hello there.. What is a Private Address or key? A locking script is an encumbrance placed on an output, and it specifies the conditions that must be met to spend the output in the future. And their first goal is to collate these transactions into what's known as a transaction block. Messages, including transactions and blocks, are propagated from each node to the peers to which it is connected. Bitcoin script has married the ideals of transparency and security using the SHA cryptographic hash function. And I'm going to talk about that concept in a subsequent video. As with real life, the bitcoin application can use several strategies to satisfy the purchase amount: Once that is complete, the bitcoin are transferred from one address to another. Recent posts CoinTracking Review: If you recall, a person issuing a transaction in Bitcoin can allocate or set aside a certain amount of money-- maybe it can be a Bitcoin or a fractional Bitcoin-- for the node who succeeds in coming up with the actual proof of working, and effectively the node that succeeds in being able to add that transaction to the overall bitcoin transaction block chain. And in fact, every transaction block as I mentioned just now incorporates the previous transaction lock. Every bitcoin transaction creates outputs, which are recorded on the bitcoin ledger. The standard for serializing signatures and lots of other things, for that matter is called Distinguished Encoding Rules DER format. When the script execution ends, you should be left with the value TRUE on the stack.
If you recall, a person issuing a transaction in Bitcoin can allocate or set aside a certain amount of money-- maybe it can be a Bitcoin or a fractional Bitcoin-- for the node who succeeds in coming up with the actual proof of working, and effectively the node that succeeds in being able to add that transaction to the overall bitcoin transaction block chain. Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed. Other cryptocurrencies use elliptic curve, too, which has been around about 30 years. Private Key: Transaction fees are calculated based on the size of the transaction in kilobytes, not the value of the transaction in bitcoin. This is a crucial function so that operations occur precisely in their desired order. The curve most bitcoins use is can you trade the movement of bitcoin libertyx bitcoin pin simple, designed for fast verification. The private key password is a randomly generated bit integer. Keep reading if you are still interested in Bitcoin script, and if you want to know more about how the script works. And I think that's reasonable. I have a imported wallet address and there are btc in it and i dont have a private key is there any way to find the private key to withdraw my funds. Hi Sudhir, great article thank you. However, you will not be able to spend it because the spending transaction, which includes the redeem script, will not be accepted because it is an invalid script. For example, this is a technique used in CoinJoin transactions where multiple where to buy bitcoins with large daily credit arch bitcoin client join transactions together to protect their privacy. A script bitcoin anonymous payment api buy bitcoin to my jaxx wallet calculating how much total bitcoin will be issued. Within that new block is the history of its transactions. Sometimes, the child might arrive before the parent. Pay-to-public-key is a simpler form of a bitcoin payment than pay-to-public-key-hash. I have all other details but how do i get back my private key. While elliptic curve cryptography provides the same level of security like RSA, it needs less computation and smaller key sizethus reducing storage and transmission requirements.
Bitcoin Script Explained
Remember, every transaction is credit debit card bitcoin exchanges bitcoin cash cryptocompare profitability by every full node on the bitcoin network. As a result, Bitcoin script avoids the unnecessarily use of complicated transactions, rather they must be relatively easy to compute. Incompleteness prevents the program from infinite loops occurring. These keys are what makes Bitcoin the safest bitcoin velocity of money bitcoin rsi graph most widely used cryptocurrency. Turing Incompleteness. Cryptographic hashing is a method for transforming large amounts of data into short numbers that are difficult to imitate. You can import it to Blockchain or any other wallet that supports importing of the private key. Because Bitcoin is not a physical currency, you cannot spend them the same way you would bitcoin mining end date bitcoin mining gpu benchmark cash even though, like cash, transactions are peer-to-peer. And I'm going to talk about that concept in a subsequent video. To log in and use all the features of Khan Academy, please enable JavaScript in your browser. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Any excess amount that remains after all outputs have been deducted from all inputs is the fee that is collected by the miners. So, understanding Bitcoin script is the essence of the value of Bitcoin transactions. Once the UTXO is selected, the wallet then produces unlocking how data mining works bitcoin tv episodes about bitcoin containing signatures for each of the UTXO, thereby making them spendable by satisfying their locking script coinbase fidelity online poker bitcoin reddit. Fun And if you want to indulge in some mindless fascination, you can sit at your desk and watch bitcoin transactions float by. Moreover, I do not need to deal with banks or currency conversion because Bitcoin is not a fiat currency. Hi Sudhir, great article thank you.
As also discussed, a transaction can require more than one signature, or a multsig , which simply means that more than one private key is necessary to unlock the script. This maintains privacy but also allows for radical transparency. She received several thousand small donations from people all around the world, totaling 50 bitcoin, so her wallet is full of very small payments UTXO. That is, the input is hashed and becomes output, and that output becomes the input of the next transaction with the Bitcoin. Finally, the valid transaction has to reach the bitcoin network so that it can be propagated until it reaches a miner for inclusion in the pubic ledger the blockchain. Of course not. Only the owner of the private key has this information. Complex script without P2SH. The instructions must specify the number of signatures required to unlock the script. These demonstrate that the script relies on the combination and correct ordering of operations for the program to execute itself correctly. In that capacity, a transaction block would basically correspond to her page in a ledger where you have multiple transactions that are listed in that page of the ledger. Many developers have tried to use the transaction scripting language to take advantage of the security and resilience of the system for applications such as digital notary services, stock certificates, and smart contracts. However, if you want to know more, just keep reading the following section as each is increasingly detailed. And what that property entails is that if you take the challenge numbers, and you take these proof numbers, and you concatenate them together, and you make them the input to a cryptographic hash function, the resulting output has to have a large prefix of zeroes And that doesn't have to be all zeroes, but a large portion of the beginning-- the prefix-- has to be all zeroes And if you think about for a moment, given that cryptographic hash functions, given that their output tends to look fairly random, it's unlikely in any given instance that you are going to see a proof. Getting a bit more complicated: One of the most interesting aspects of programming is Flow Control. But Alice shares her public key is with Bob, and both addresses are publicly available. It's going to give the aggregate over all these different transactions.
Bitcoin: Transaction block chains
This is similar to a post dated paper cheque -it might bitcoin wallet not syncing bitcoin gambling sites if it is not cashed on time. This technology allows them to prove their identity with a set of cryptographic keys: P2SH addresses are Base58Check encodings of the byte hash of a script, just like bitcoin addresses are Base58Check encodings of the byte hash of a public key. P2SH is the most common script used presently because it is more compact than the earlier version. By now you should understand many of the basic and fundamental concepts that enable the successful operation of Bitcoin Script. Become a Part of CoinSutra Community. Once recorded on the blockchain and confirmed by sufficient subsequent blocks confirmationsthe transaction is a permanent part of the bitcoin ledger and is accepted as valid by all participants. Figures and show in two parts a step-by-step execution of the combined script, which will prove this is a valid transaction. But they're also going to be getting information about a lot of other transactions that are taking place around the same time. Find the smallest greater. Hi Sudhir, does minergate use a pool bitcoin games online article thank you. Like all asymmetric encryption, the ECDH problem can be solved. A script that calls the blockchain.
Private keys are not bought and sold. Try validating the preceding script yourself using pencil and paper. The same way it is possible to add another signature to the script, verify can be added to the sequence of opcodes. For example, a 2-of-3 multi-signature is one where three public keys are listed as potential signers and at least two of those must be used to create signatures for a valid transaction to spend the funds. There may be an instance where 5 signatures are needed because there are 5 partners involved in the transaction. Really, what they're starting to do is starting to work off of a new, updated transaction block chain. Email Address. Each transaction included as a block in the blockchain has the history of the previous transaction. Pay-to-public-key is a simpler form of a bitcoin payment than pay-to-public-key-hash. To own bitcoin is to have in your possession a complete history of the transactions.
What People are Reading
For Bitcoin transactions, to unlock and spend a transaction, the sender must have the corresponding private key on the blockchain so that she can spend the funds. You can import it to Blockchain or any other wallet that supports importing of the private key. Great knowledge Sudhir! So if you recall in the previous video, you had a motivating example of a user, Alice, who wanted to send some number of Bitcoins to another user, Bob, in the system. This is the address used to publicly receive bitcoins. Copy Link. So if im using a hardware wallet like neon for example to store neo. From the 1 to the H is a valid bitcoin address. Every time a valid block is generated miners get a reward in the form of newly minted BTC. Desktop Wallets Desktop wallets are relatively safe. What it does is hold my bitcoin address, which keeps a record of all of my transactions, and therefore of my balance. All right, now once this proof of work is found, let's say that the proof of work is eventually found. P2SH addresses hide all of the complexity, so that the person making a payment does not see the script. The private key must always be kept secret and never shared with other people. Private Key: Only when the item at the top of the stack is TRUE is the transaction valid. Once a transaction has been verified by the miners, a block is added to the blockchain. Moreover, the signatures are mathematically related to Bitcoin addresses.
Trezor was the first hardware wallet to be launched since the invention of Bitcoin. Okay, thanks. P2SH shifts the burden in data storage for the long script from the output which is in the UTXO set coinbase verify id bitcoin with credit car therefore affect memory to the ethereum mining speed calculator hd7950 2019 980 ti hashrate litecoin only stored on the blockchain. May 22, Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed. I have downloaded different bitcoin wallet app and usually I can only find functions like Send, Receive, Buy etc…. A cryptographically generated alphanumeric sequence is produced hashing24 or bitcoin.com how profitable is mining bitcoins prove the operation occurred. Pay-to-script-hash P2SH was developed to resolve these practical difficulties and to make the use of complex scripts as easy as a payment to a bitcoin address. Whenever a user receives bitcoin, that amount is recorded within the blockchain as a UTXO. Bitcoin Calculator: Bitcoin Script is the programming language that makes the digital transactions of the currency possible and traceable. Turing Incompleteness. The miners must, therefore, solve the computation to ensure that the private keys match the details of the transaction. Hi Sudhir, i just had a question. I have a Trezor linked account a lock appears next to it where I keep nearly all my bitcoins. In multi-sig transactions, all people must verify the transaction for the outputs to be unlocked. A private key is secret, as indicated by its .
