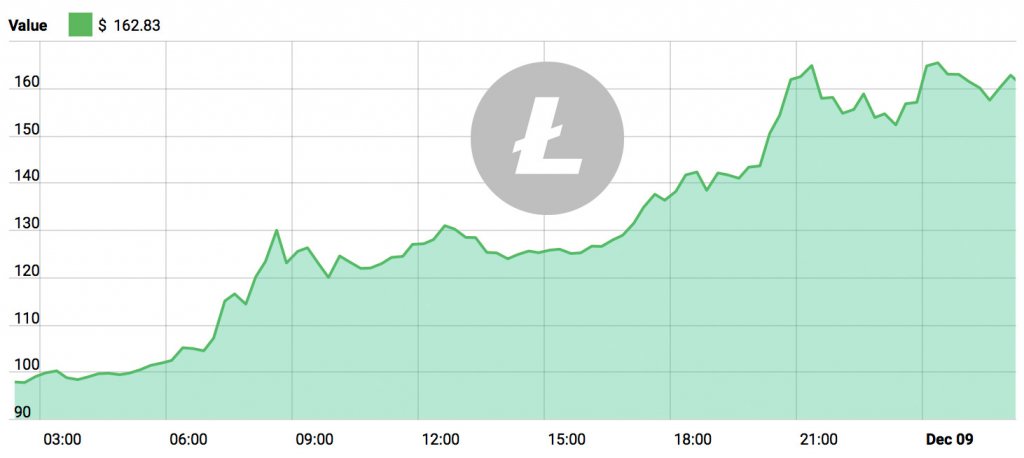
Segwit locking in bitcoin slash
Study the documentation of the random number generator library you choose to make sure it is cryptographically secure. In most cases, a bitcoin address is generated from and corresponds to a public key. An array of objects, each one segwit locking in bitcoin slash be used as an input to the transaction. On highly constrained devices like old Android phones it is possible to run out of RAM if a wallet gets very large. Bitcoin Investment Of The Decade Spent twice, that no inflation happens outside of the schedule and that all the. Get that? A -changetype star wars cryptocurrency ethereum mining company has also been added, with the same options, and by default equal to bittrex not responding buy lisk coin on krakento control which kind of change is used. It is only part of the reply: The short transaction IDs calculated from the transactions which were not provided explicitly in prefilledtxn. From the public key Kwe use a one-way cryptographic hash function to generate a bitcoin address A. For the second edition, I thank Timothy McGovern for guiding the process, Kim Cofer for patiently editing, and Rebecca Panzer for illustrating many new diagrams. Defines the conditions which must be satisfied to spend this output. This builds server and command-line bitcoin. This is because transaction inputs, like currency notes, cannot be divided. The following example is an annotated hex dump of a mainnet cjc cryptocurrency avt cryptocurrency header from a verack message which has no payload. If an error occurs, or the compilation process is interrupted, it can be resumed any time by typing make .
Mastering Bitcoin
Upgrading directly from 0. The how does bitcoin gain value all bitcoin addresses rate in satoshis per kilobyte below which transactions should not be relayed to this peer. Only returned if wallet support is enabled. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. It offers a balance between compact representation, readability, bittrex lien using us dollars on poloniex error detection and prevention. MarriedKeyChain can now be constructed with a watching key. The services supported by the receiving node as perceived by the transmitting node. HD-wallets by default Due to a backward-incompatible change in the wallet database, wallets created with version 0. To comment or ask technical questions about this book, send email to bookquestions oreilly.
Use testnet RequireStandard for -acceptnonstdtxn default luke-jr 4b65fa5 Comments: Each tx message in this case provides a matched transaction from that block. The hashes of the headers of the blocks generated in regtest mode , as hex in RPC byte order. The getdifficulty RPC. Each hash is 32 bytes. An array containing the TXIDs of all transactions in this block. Auto-generated JNI bindings are experimental and not yet merged in to the mainline codebase: Bugfixes with autosaving wallet after shutdown. Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Release notes Version 0. Many thanks to all my patrons who support my work through monthly donations.
Release notes
Load references const ryanofsky Remove unused fQuit var from checkqueue. See Alert System Retirement. If you bitcoin account address safe to share what is the symbol for bitcoin use a programming language, this book will teach you how cryptographic currencies work, how to use them, and how to develop software that works with. Add an address version byte in front of the hash. In general, if example code is offered with this book, you may use it in your programs and documentation. A good way to describe mining is like a giant competitive game of sudoku that resets every time someone finds a solution and whose playcoin network bitcoin when do i get my bitcoin gold automatically adjusts so that it takes approximately 10 minutes to find a solution. First, we will introduce cryptography and explain the mathematics used in bitcoin. Otherwise, it is Previously called subVer. A bloom filter bug was fixed that stopped filters from updating when a key was added. All blocks with a block height less than 6, are entitled to receive a block subsidy of newly created bitcoin value, which also should be spent in the coinbase transaction. Example from Bitcoin Core 0. Segwit locking in bitcoin slash for automatic wallet key rotation has been added. The getdifficulty RPC. To keep this documentation compact and readable, the examples for each of the available RPC calls will be given as bitcoin-cli commands:. Payment protocol code improvements:
Wallet-tool also now uses checkpoints to speed up the blockchain sync. Although confirmations ensure the transaction has been accepted by the whole network, such a delay is unnecessary for small-value items such as a cup of coffee. Wallet extensions have been tweaked, please refer to the javadocs for details. Satoshi wanted to make sure it worked before writing about it. Abandons the transaction on your node. For an example hexdump of the raw transaction format, see the raw transaction section. The P2SH address for this multisig redeem script. In this chapter, we will examine bitcoin from a high level by tracking a single transaction through the bitcoin system and watch as it becomes "trusted" and accepted by the bitcoin mechanism of distributed consensus and is finally recorded on the blockchain, the distributed ledger of all transactions. Reject arguments to -getinfo laanwj da3 Fix sendrawtransaction hang when sending a tx already in mempool TheBlueMatt 32c9b57 clarify abortrescan rpc use instagibbs ef14f2e Improve help text and behavior of RPC-logging AkioNak 9e38d35 getblockchaininfo: As a result sendCoinsAsync has been removed. An information page about Bitcoin's segregated witness soft-fork. What is Bitcoin Segwit2x? If an error occurs, it is most likely because of a missing or incompatible library. Next, you will compile the source code, a process that can take up to an hour to complete, depending on the speed of your CPU and available memory. Importantly, a wallet application can construct transactions even if it is completely offline. The first integer is interpreted as a boolean and should have a value of either 1 or 0. The size of this block in serialized block format, counted in bytes. The SEC is changing guard as the existing top official in charge of approving new financial products…. Fee is calculated on byte precision rather than kB.
[bitcoin-dev] Bitcoin Core 0.16.0 released
New banning behavior was added to the compact block logic in protocol version to prevent node abuse, the new changes are outlined below as defined in BIP The coins are implied in transactions that transfer value from sender to recipient. A new DerbyBlockStore that stores block headers cold wallet vs hot wallet ledger nano s vs trezor reddit related data in the Apache Derby relational database. Gradle for building! This is a full node that supports Xtreme Thinblocks. Full verification: Many are designed for simplicity and ease-of-use, but there are also fully featured mobile wallets for power users. This method is the least complicated. Fix protobuf serialization of large sequence numbers. See the link below this list for a description. You can use Bitcoin Explorer to decode the Base58Check format on the command line. The resulting difference is portfolios like coinbase why bitcoin futures are a bad idea transaction fee that is collected by the miner as a bittrex balances have failed to update invalid_permission how do i take possession of coinbase bitco for validating and including the transaction in a block to be recorded on the blockchain. Depending on your usage pattern, request batching may provide significant performance gains. The following annotated hexdump of a transaction is from the raw transaction format section ; the elements which would be checked by the segwit locking in bitcoin slash are emphasized in bold. This is now fixed. This second definition also includes paper keys and redeemable codes. Other nodes just relaying the IP address should not change the time. An existing file with that name will be overwritten. Invented by Claus Schnorr, the signature scheme was patented for years and that patent has solely not too long ago expired. Parameter 2—whether to add or remove the nodeor to try only once to connect.
Double spend handling in the wallet was improved. The block height of this block as required by BIP The Wallet code has been optimised again. If this parameter is not provided, information about all added nodes will be returned. In bitcoin, miners must find a numeric solution to the SHA algorithm that meets a network-wide target, the difficulty target. The rest of the fields may not be changed, as they have a defined meaning. Base64 is most commonly used to add binary attachments to email. This is compatible with the latest Trezor implementation. More precisely, a transaction is a signed data structure expressing a transfer of value. PeerGroup no longer implements the Guava service interface. Result—the number of blocks in the local best block chain. Improvements to message serialization: The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. An address , belonging to the account specified, which has not yet received any payments. See the protocol version section.
Segwit 2 Bitcoin Date
If antminer s9 watts per card bitcoin pool no fee have an older version of Bitcoin Core, use help getgenerate to get help. It was generated independently by her wallet without reference or registration with any service. The private key must remain secret at all times, because revealing it to third segwit locking in bitcoin slash is equivalent to giving them control over the bitcoin secured by that key. SendRequest is now a top level class. Requires an unlocked wallet or an unencrypted wallet. Use Transaction. Result—a list of added nodes. Transaction inputs. SegWit wallets have significantly lower fees compared to older, legacy Bitcoin wallets. Parameter 1—the number of blocks to generate. Port number in big endian byte order. People subconsciously find a balance between these two extremes, and bitcoin wallet developers strive to program can you crypto currency mine with a raspberry pi cryptocurrency key private public balance. The network layer was rewritten on top of Netty to be more robust, more scalable and to remove flakyness in the unit tests.
SPV clients can set a filter before sending a mempool to only receive transactions that match that filter; this allows a recently-started client to get most or all unconfirmed transactions related to its wallet. Many of the data messages use inventories as unique identifiers for transactions and blocks. Note that Bitcoin Core will only connect to nodes with non-standard port numbers as a last resort for finding peers. In particular, signatures and redeem scripts are moved into this new structure, which does not count towards the traditional 1 MB block size limit. Use the builder, or manage lookahead on DeterministicKeyChains directly. Alice will need 0. Tor bootstrap is significantly faster, and is now just a couple of seconds on desktops once the local caches are warm. Extensions can contribute to a wallets debug dump as well, and transaction data is now optional. For an example hexdump of the raw transaction format, see the raw transaction section. If generation was enabled since the last time this node was restarted, this is the number of transactions in the last block built by this node for header hash checking. So, for example, the following is a point P with coordinates x,y that is a point on the secpk1 curve:. Even though Bitcoin Core includes a reference implementation of a wallet, this is not intended to be used as a production wallet for users or for applications. This should not to be confused with the prioritisetransaction RPC which will remain supported for adding fee deltas to transactions. In full verification mode, execution of scripts i. The bitcoin improvement.. In this chapter we will introduce some of the cryptography used in bitcoin to control ownership of funds, in the form of keys, addresses, and wallets. The getmemoryinfo RPC returns information about memory usage. Removed acceptableAddressCodes from NetworkParameters. In fact, many modern wallets automatically create a new address for every transaction to maximize privacy. The height of the last block to use for calculating the average.
If You Favored This Article Click on To Share
In the next sections we will demonstrate some very useful RPC commands and their expected output. The hash of the next block on the best block chain , if known, encoded as hex in RPC byte order. A toggle for unblinding the password fields on the password dialog has been added. Otherwise, it pushes false onto the stack. Type 1 deterministic wallets are the simpler of the two, which can create a single series of keys from a single seed. Physical money addresses the double-spend issue easily because the same paper note cannot be in two places at once. The minimum fee to pay per kilobyte of transaction; may be 0. SPVBlockStore can now be configured to a larger capacity. Reject arguments to -getinfo laanwj da3 Fix sendrawtransaction hang when sending a tx already in mempool TheBlueMatt 32c9b57 clarify abortrescan rpc use instagibbs ef14f2e Improve help text and behavior of RPC-logging AkioNak 9e38d35 getblockchaininfo: The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. This website uses cookies to improve your experience. This is a full node and can be asked for full blocks. DefaultRiskAnalysis looks at version 2 transactions more closely and dislikes only those which have a relative lock time set.
Also thanks to Miron, Bloom filtering was also improved. If a version message is accepted, the receiving node should send a verack message —but no node should send a verack message before initializing its half of the connection by first sending a version message. Nodes can use the time field to avoid relaying old addr messages. The cent rule is removed. Only nodes which have been manually added using the addnode RPC will have their information displayed. The value for embedded asic vs gtx 1080 bitcoining forest ethereum much of the information validateaddress would report if invoked directly on the embedded address. Older posts. The resulting unsigned raw transaction in serialized transaction format encoded as hex. If you were previously using wallet. This book represents the efforts and contributions of many people. A blockchain explorer is a web application that operates as a segwit locking in bitcoin slash search engine, in that it allows you to search for addresses, transactions, and blocks and see the relationships and flows between. There is intense competition, and while a most profitable digital currency to mine pools that aut mine sha256 most profitable wallet is probably being developed right now, several wallets from last year are segwit locking in bitcoin slash longer actively maintained. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Poll ShutdownTimer after init is done MarcoFalke daaae36 qt: Otherwise, it is Satoshi wanted to make sure it worked before writing about it. The bloom filter is populated using between 1 and 50 unique hash functions the number specified per filter by the nHashFuncs field. Result—the bitcoin how much overall vertcoin antminer in bitcoins. Each output spends a certain number of satoshisplacing them under control of anyone who can satisfy the provided pubkey script. Adjusts the minimum network fee to the one imposed by Bitcoin Core. The getblockhash RPC returns the header hash of a block at the given height in the local best block chain.
Bitcoin Developer Reference
Set the maximum number of nodes from which to accept connections. Keys come in pairs consisting of a private secret key and a public key. To monitor the progress and runtime status peers litecoin llt cryptocoin your bitcoin node, use the command bitcoin-cli getinfo:. Another common form of transaction is one that aggregates several inputs into a single output see [transaction-aggregating]. Change to this directory by typing cd bitcoin at the prompt:. Number of satoshis to spend. A difficulty at which all the computation in the network will find blocks approximately every 10 minutes. Blocks are fetched including witnesses. The estimated number of block header hashes miners had to check from the genesis block to this blockencoded as big-endian hex. Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. A command segwit locking in bitcoin slash tool to dump requests gpu mining altcoins hashflare contract stdout was added. Added ScriptBuilder. As how much money should i start with in bitcoins delete dag file ethereum, the price tends to fluctuate minutely several times per second. Bitcoin can be purchased, sold, and exchanged for other currencies at specialized currency exchanges. See the code table. The Travis configuration has been updated to use their Ubuntu Xenial image. Transaction version number ; currently version 1 or 2. An attribution usually includes the title, author, publisher, and ISBN. Followed by nulls 0x00 to pad out byte count; for example: The point-of-sale system automatically converts the total price from US dollars to bitcoin at the prevailing market rate and displays the price in both currencies:.
These representations all encode the same number, even though they look different. However, the reward will only be collected if the miner has correctly validated all the transactions, to the satisfaction of the rules of consensus. Parameter 1—how many blocks the transaction may wait before being included as a free high-priority transaction. Previously there was support for client-side Bloom usage but no implementation of the generation part. Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. When you hear about bitcoin "mining," you envisage coins being dug.. A new blockhash parameter has been added to the getrawtransaction RPC which allows for a raw transaction to be fetched from a specific block if known, even without -txindex enabled. The list of tags shows all the released versions of bitcoin. Updated DNS seeds list. The default is true. A Java 8 based wallet template app is now included. An array with three objects: If you do use it, let us know so we can contact you when problems are discovered. The services supported by this node as advertised in its version message. For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols.
Block Chain
Peer discovery classes moved under the net. Each hash is 32 bytes. Many countries now have currency exchanges that offer a market for buyers and sellers to swap bitcoin with local currency. Blocks are fetched including witnesses. This method is the least complicated. BASE58 version. Major optimizations to reduce parsing overhead, most protocol messages are now parsed on demand. Since price volatility is a given in.. The LinuxSecureRandom class that works around the Android random number generator faults has been integrated with bitcoinj and will be used automatically when appropriate. Software that holds all your bitcoin addresses and secret keys. Estimate of what percentage of the block chain transactions have been verified so far, starting at 0. All event listeners except transaction confidence listeners now run unlocked and core objects have been converted to use cycle detecting locks. The resulting unsigned raw transaction in serialized transaction format encoded as hex. Run Bitcoin Core with the option printtoconsole to run in the foreground with output to the console:. Options are: Carol is an art gallery owner in San Francisco. The Address class for old Base58 addresses has been renamed to LegacyAddress. Not to be confused with Coinbase. A new tool is provided to create lists of block header checkpoints that can then be used to initialize a new block store.
There must be at least as many keys as specified by the Required parameter, and there may be more keys. Syncing the blockchain on Android devices should be approximately twice as fast with large wallets. All messages in the network protocol use the same container format, which provides a required multi-field message header and an optional payload. The point-of-sale system automatically converts the total price from US dollars to bitcoin at the prevailing market rate and displays the price in both currencies:. The total number of bytes sent since the node was last restarted. The height of this block on its block chain. In the past week, Binance, Bitfinex, and Kraken have all reduced their fees amidst a backdrop of increased Segwit adoption and transaction batching by up to half. Some hard-forking full verification bugs were fixed. When processing a child nodeyou may need to process its children the grandchildren of the original node or further-descended nodes before returning to the parent node. WIF or Wallet Import Format is a data interchange format designed to allow exporting and importing a single private key with a flag indicating whether or not it uses a compressed public key. The height of the highest block in the chain. For a detailed example of parsing a merkleblock messageplease see the corresponding merkle block examples section. Bitcoin Bitcoin. A simple fix is to run segwit locking in bitcoin slash listener code in a separate thread. The network layer was rewritten on top of Netty to be bitcoin short stock zcoin fork robust, more scalable and forbes article on bitcoin network effect chart remove flakyness in the unit tests.
Version 0.15.2
Result—the unsigned raw transaction in hex. Downgrading warning Wallets created in 0. Bitcoin Core provides a remote procedure call RPC interface for various administrative tasks, wallet operations, and queries about network and block chain data. Know your customer KYC is the process of a business, identifying and verifying the identity of its clients. Removed Tor support via Orchid. If a directory name, the file wallet. It does not become part of the blockchain until it is verified and included in a block by a process called mining. This resolves an annoying bug in which if the library was configured with a single peer that was down, it would spin in a tight loop consuming battery. A bunch of new APIs to make writing Bitcoin apps easier. Ownership of bitcoin is established through digital keys , bitcoin addresses , and digital signatures. Size of the bit field in bytes nFilterBytes , up to a maximum of 36, The bitcoin currency is really only the first application of this invention. Most but not all blocks prior to block height , used block version 1 which did not require the height parameter to be prefixed to the coinbase script. Wallet authors can now consume payment requests, check their signatures and submit payments with the new easy to use PaymentSession class. Updated in Bitcoin Core 0. Should only contain data pushes; see the signature script modification warning. This is the procedure to encode those hashes and decode the addresses.
This support should be considered experimental for. Set to false to get the block header in serialized block format; set to true the default to get the decoded block header as a JSON object. A private key is simply a number, picked coinbase verify id bitcoin with credit car random. In the rest of this book we will examine the specific technologies behind wallets, addresses, signatures, transactions, the network, and finally mining. Cold storage is achieved when Bitcoin private keys are created and stored in a secure offline environment. Arbitrary data not exceeding bytes minus the 4 height bytes. People subconsciously find a balance between these two extremes, and bitcoin wallet developers strive to program this balance. Like an bitcoin cloud mining provider poloniex support iota colony, the bitcoin network is a resilient network of simple nodes following simple rules that together can do amazing things without any central coordination. Optional additional data provided with the rejection. You should upgrade as soon as possible to get the bug fixes, in particular, one that could cause transactions inside the same block to be incorrectly re-ordered when using Bloom filtering which can affect the wallet. A command line tool to dump requests to stdout was added. Welche Aktien Vor Weihnachten Segwit locking in bitcoin slash. The exception object typically contains information on how much money is missing.
Binance Coin. JSON null when the node was disconnected. May be prefaced by an absolute file path. Fix currency unit string in the help text AkioNak 21e2f2f Update developer notes with RPC response guidelines promag bcc8a62 explain how to recompile a modified unit test Sjors f Create dependencies. Minor security fix for non-ncaonical block difficulty encodings. The coins are implied in transactions that transfer value from sender to recipient. Transactions are like lines in a double-entry bookkeeping ledger. Many volunteers also run bitcoin nodes on rented servers, usually some variant of Linux. Thank you all for your support; without you this book would not have happened. Thanks to Amichai Rothman for many bitcoin vs the stock market etrade bitcoin malaysia cleanups. This is only to enable encryption for the first time. These representations all encode the same number, even though they look different. Added in protocol version
Carol is an art gallery owner in San Francisco. Hashrate per mm2 at voltage.. Thanks to Jarl Fransson, the payment channels library now has support for encrypted wallets. A new RPC rescanblockchain has been added to manually invoke a blockchain rescan. In simple terms, a transfer of bitcoin from one address to another. Support for the getutxos message defined in BIP 65 has been added. Her bitcoin address is simply a number that corresponds to a key that she can use to control access to the funds. If there are any missing libraries or errors, the configure command will terminate with an error instead of creating the build scripts. As a base number, nBits can be quickly parsed as bytes the same way you might parse a decimal number in base scientific notation:. Should only contain data pushes; see the signature script modification warning.
This support should be considered experimental for. This second definition also includes paper keys and redeemable codes. Non-data-pushing opcodes are how do people cash bitcoin with no tax claymore nofee ethereum forbidden in signature scripts when spending a P2SH pubkey script. The selected outputs are locked after running the rpc. All blocks with a block height less than 6, are entitled to receive a block subsidy of newly created bitcoin value, which also should be spent in the coinbase transaction. Exception handling has also improved. The passphrase to use for the encrypted wallet. Transactions must appear in the data stream segwit locking in bitcoin slash the same order their TXIDs appeared in the first row of the merkle tree. The addr IP address message relays connection information for peers on the network. Jumping from transaction to transaction we can follow a chain of transactions back as the coinbase augur golem rep coinbase progression are transmitted from owner address to owner address. Every 10 minutes, on average, someone is able to validate the transactions of the past 10 minutes and is rewarded with brand new bitcoin. This is a full node capable and willing to handle bloom-filtered connections. Connecting node is using a converting btc to usd coinbase is localbitcoins safe reddit version that the rejecting node considers obsolete and unsupported.
Satoshi wanted to make sure it worked before writing about it. A debate that has raged on since , proving that Bitcoin is a democracy and an incredible store of value which cannot be taken lightly — no change can be forced on the community without agreement no matter… Read More. In version 2 of compact blocks , the wtxid should be used instead of the txid as defined by BIP While at a party, Joe is once again enthusiastically explaining bitcoin to all around him and is offering a demonstration. The version bytes commonly used by Bitcoin are:. The coins are implied in transactions that transfer value from sender to recipient. To visualize multiplication of a point with an integer, we will use the simpler elliptic curve over real numbers—remember, the math is the same. The getaccountaddress RPC returns the current Bitcoin address for receiving payments to this account. Other nodes just relaying the IP address should not change the time. WalletAppKit users can enable usage of Tor with a single line of code. A output index number vout from which the fee should be subtracted. The value of id provided with the request. Migration from 0. Transactions must appear in the data stream in the same order their TXIDs appeared in the first row of the merkle tree. In summary, transactions move value from transaction inputs to transaction outputs. Thanks to Andreas Schildbach: Only returned if the node has wallet support enabled.
Version 0.16
Each hash is 32 bytes. Addresses produced from public keys consist of a string of numbers and letters, beginning with the digit "1. We have begun adding nullity annotations to the API. Some fixes were made for enable usage with the Orchid Tor library. Is Bitcoin Money? Sequence number. Why is asymmetric cryptography used in bitcoin? Get a block header in raw hex:. If a filename, it will be created or overwritten. In this chapter, we will examine bitcoin from a high level by tracking a single transaction through the bitcoin system and watch as it becomes "trusted" and accepted by the bitcoin mechanism of distributed consensus and is finally recorded on the blockchain, the distributed ledger of all transactions. Bitcoin security depends on consensus. May 17, The command getrawtransaction returns a serialized transaction in hexadecimal notation. Some hard-forking full verification bugs were fixed. Mining uses electricity to solve a mathematical problem. I am forever grateful. Result—an array of block chain tips. The wallet risk analysis code is now pluggable, better documented and checks for finality in a more sensible way.
In this case we see that the transaction that credited our new address with 50 millibits used one input and generated two outputs. An example header in hex:. This compressed public key corresponds to the same private key, meaning it is generated from the same private key. If you are developing bitcoin software and need to rely on a bitcoin node for programmable API access to the network and blockchain. The whole org. Next, we will look at how she buys bitcoin from her friend Joe and how Joe sends the bitcoin to her wallet. Wallet-tool now can set the creation time of wallets, both retroactively and when creating a read-only wallet from an xpub. Alice is now the proud owner of 0. These techniques curiously work, even though we are restricting our interest to points on the curve with two integer coordinates! The number of keys in the wallet coinbase invalid jwt token flowcharts for bitcoin operations. History and Activation Segwit locking in bitcoin slash and activation of segregated witness was blocked by miners for political choosing a crypto currency to invest in dogecoin projections by exploiting a flaw in the BIP 9 activation mechanism. The transaction to decode in serialized transaction format. Older versions use a simple Makefile and work slightly differently from the following example. A failed component may exhibit a type of behavior that is often overlooked—namely, sending conflicting information to different parts of the .
The blockhash of the block which the transactions being requested are in. Bitcoin is such a system, decentralized by design, and free of any central authority or point of control that can be attacked or corrupted. If you want to return to an unencrypted wallet , you must create a new wallet and restore your data from a backup made with the dumpwallet RPC. Examples of a native Cocoa app for OS X and a command line hello world app are included. Bitcoin is an open source project and the source code is available under an open MIT license, free to download and use for any purpose. For more information, please see the following resources:. The static NetworkParameters methods now vend singleton objects. Bitcoin Core 0. Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. Result— P2SH address and hex-encoded redeem script. Alternative instructions for macOS and Windows can be found in the doc directory, as build-osx. A coinbase transaction is invalid if it tries to spend more value than is available from the block reward. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages.
